By Patrick Sullivan, Film & TV Editor
An Epigram investigation has found that student and staff emails fell victim to the largest phishing attack against the University earlier this month.
The attack generated thousands of unique web links designed to steal login credentials.
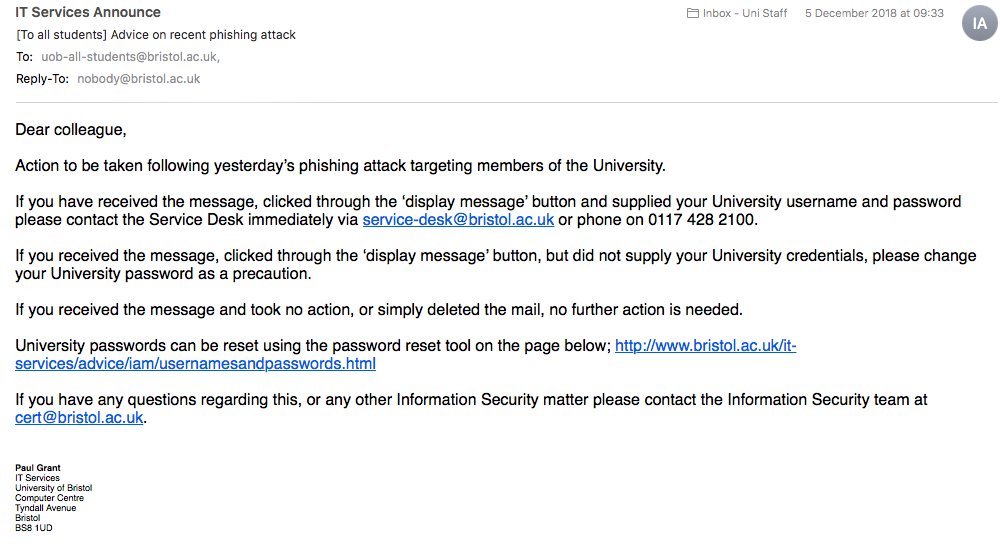
According to IT Services, it is likely to all have started by one member of the University falling victim to an email from an external source, giving away their account details to the unknown fraudster.
By the end of a 72 hour period, around 450 accounts had been compromised, nearly 2,000 calls had been received by the IT Service Desk, and several thousands of students and staff had received dangerous emails from a range of University and non-University addresses.
December 4, 2018 2:37PM GMT
— Bristol Uni IT news (@BristolUniIT) 4 December 2018
Identified - We are receiving a spate of phishing emails, from compromised UOB accounts. These are replies from legitimate emails, but have a green ...https://t.co/fx4eWKIcpO
Epigram spoke to Matt Osborn, the University’s Information Security Manager, about the incident, who said: ‘It was noticed that the sophistication of this attack and the level of impact it was having on our staff and students was beyond what we had seen before, so, at that point, [IT Services] instigated our major incident process.’
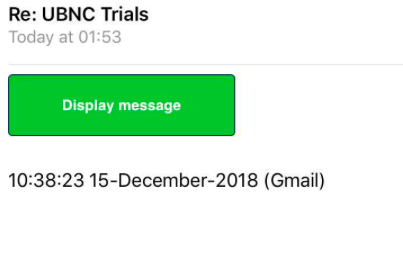
The sophistication of the attack refers to the written script which sent emails from newly compromised accounts and continuously created new links.
Within the URL of the web addresses, there was 78 domains identified by IT Services, but several thousands of sub-domains. The sheer amount of addresses prevented the University from simply blocking the websites.
Contributing to the allure of the scam was the script’s ability to retrieve subjects of past emails within a compromised account, which meant the emails were titled in the format ‘RE: Aerosoc Sign Up and Events’ and seemed more legitimate to the recipients than traditional phishing emails.
Epigram / Imogen Horton
Osborn added: ‘The days of these attempts to steal people’s passwords and install malicious software being basic and obvious to see are over.’
'There will be people thinking “I will never fall for that”. We saw from how effective the messages were on [December 4] that if [the email] is a subject that is recognised, [you] are far more likely to click on it.’
Members of IT Services Information Security and the Digital Workspace team focused their attention on identifying recognisable characteristics of these emails to prevent staff and students from receiving them.
They told Epigram: ‘We’re in a contained position where we’re not seeing any further compromised accounts. The controls we’ve put in place are adequate to stop what we saw last week.’
The passwords have been changed for all of the compromised accounts.
Epigram / Imogen Horton
Osborn also highlighted that other universities, including UWE, Cardiff and Reading, have suffered with similar attacks.
He said: ‘Any organisation, to a certain degree, is vulnerable to this, and the impact of a security incident is massive.’
'IT Services works hard to protect students and staff but the security of our systems and information is everyone's responsibility.
'We are monitoring, responding and planning against these types of threats but our best defence is an informed community that understands the value of the systems they use and takes protecting them seriously.'
IT Services recommend students not reuse passwords between accounts - using password managers instead - keep devices up-to-date and set up two factor authentication. You can request the latter from the IT Service Desk for your Microsoft Office 365 University account.
Featured Image: Unsplash / John Schnobrich
Were you affected by the phishing emails? Let us know!